Odin:1 - Walkthrough [Vulnhub]
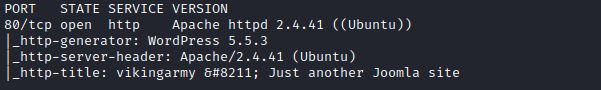
Here's my solution for Odin:1. The machine can be downloaded from here. Service Discovery Using nmap to scan all TCP ports. $ nmap -sC -sV -p- 192.168.1.106 We find only 1 port open. Enumeration We map ip to host by editing the /etc/hosts file. Lets browse the web. We find that the web in built on CMS - Wordpress. Scrolling down, we see some base32 encoded text. We can browse CyberChef to decode it. This seems like a hint- To use rockyou wordlist. We run wp-scan to enumerate all plugins and users. $ wp-scan --url http://odin -e ap,u No plugins were found but we found a user- odin. When we try to manually verify the user- odin, it says- unknown username. Now we enter a default user name - admin and a random password. After reading the error we confirm that the user- admin exits. Since we do not have the password for the user. We user wpscan to brute force the password. $ wpscan --url http://odin/ -U admin -P /usr/share/wordlists/rockyou.txt We get the password as- qwerty Let