Kira:CTF - Walkthrough [Vulnhub]
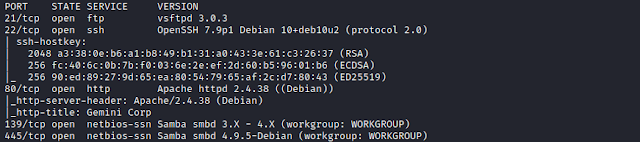
Here's my solution for Kira:CTF. The machine can be downloaded from here. Service Discovery Using nmap to scan all TCP ports. $ nmap -sC -sV -p- 192.168.1.105 We find only 1 port open. Enumeration Browsing the web, We see an upload option, lets go for it. We try to upload the php reverse shell file. Seems there's some kind of validation which does not allows php files. Now we upload the same php reverse shell file by adding an image extension to it. i.e rshell.php > rshell.php.jpeg Seems that we have successfully upload the file. We navigate to /uploads and here we find the uploaded reverse shell file. Back to the main web page, here we find a language button. We click the language button. Again we click the language button. We find that the lang= parameter is vulnerable to LFI. Initial Access Now to run the php reverse shell file we simply browse the location of the file. And on the other hand we start the netcat listener. We get the shell. Privilege Escalation From www-dat