Relevant:1 - Walkthrough [Vulnhub]
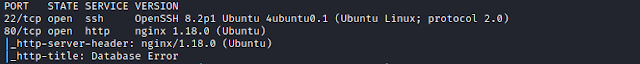
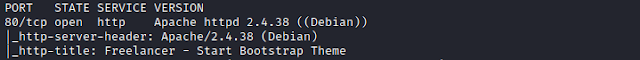
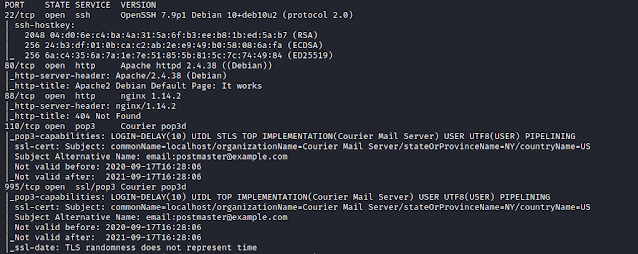
Here's my solution for Relevant:1. The machine can be downloaded from here. Nmap Scanning for all TCP ports. $ nmap -sC -sV -p- 192.168.1.109 We find 2 port open. Enumeration Browsing website, the web page presents us with 3 links, seems some kind of hints, lets check it out. Browsing the 1st link- https://rb.gy/g5prrv, gets redirect to youtube. Browsing the 2nd link- https://pastebin.com/sGzQSQXu, seems like a list of credentials. Just a thought, the home page says- because we hax0r3d your webz!, meaning the hacker has compromised the website. So, may be they have leaked the credentials here. Tried brute forcing the ssh but no result. Browsing the 3rd link- https://ibb.co/JtTY0Md, the QR code. We can browse Zxing, and decode it. Interesting, we keep it we may require at further stages. Lets scan for directories. $ dirb -u http://192.168.1.109 -r Seems like the website is built on CMS- Wordpress. We can use wpscan to enumerate it further. $ wpscan --url http://192.168.1.109 -e