KB-VULN:3 - Walkthrough [Vulnhub]
Here's my solution for KB-VULN:3.
The machine can be downloaded from here.
Port Scanning
Using nmap to scan all TCP ports.
$ nmap -sC -sV -p- 192.168.1.105
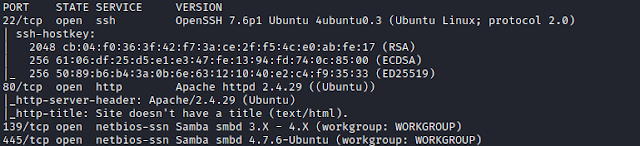
We find 4 ports open.
Enumeration
Browsing the web and checking the source page did not reveal much information or any hint.

As SMB ports are open lets enumerate it.

Lets get the smbshell.

We download the zip file- website.zip
While unzipping the file, it asks for password.

As we do not the password we can try to brute force.
After unzipping we get one of the file named as README.txt which contains credential and a website named as kb.vuln

So, we map ip to hostname by editing the /etc/hosts file.
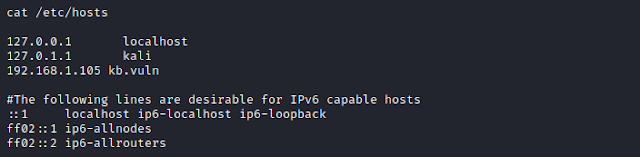
Now lets again browse the web with domain name.

We see that the website is built on CMS- Sitemagic. We search for the exploit and we find it here.
After reading the exploit we login with the found credential.
Username: admin
Password: jesse
And navigate to Content > Files > Images

We click on upload to upload the php reverse shell file.

Getting Access
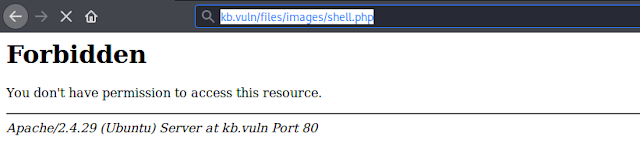
To run the php reverse shell file/exploit we browse the URL /file/images/shell.php
And on the other hand we start the netcat listener.

Privilege Escalation
We check for SUID permission.

We navigate to /dev/shm directory and place the exploit here.

Lets run the exploit and on the other hand we start the netcat listener.









Comments
Post a Comment