FishyMail:1 - Walkthrough [Vulnhub]
Here's my solution for FishyMail:1
The machine can be downloaded from here.
Port Scanning
Using nmap to scan all TCP ports.
$ nmap -sC -sV -p- 192.168.1.106
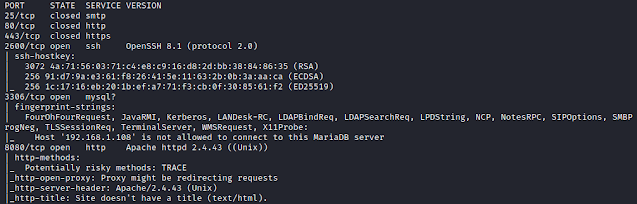
We find 3 ports open.
Enumeration
Browsing the web hosted on port 8080. Checking the source page did not reveal any useful information/hint.

Using dirb to scan directories.
$ dirb http://192.168.1.106:8080 -r

Having a look at /robots.txt

Interesting, browsing /dataentry.

Again using dirb to brute force /dataentry directory.
$ dirb http://192.168.1.106:8080/dataentry/

Browsing /dataentry/backup/admin/files, still no any useful information.

Again we try to brute force but this time with some extension.
$ gobuster dir -u http://192.168.1.106:8080/dataentry/backup/admin/files/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt

Interesting, Browsing the /dir.txt

After decoding the double base64 encoded data the output seems to be like credentials. We can try these over ssh.

Getting Access
Accessing SSH.
$ ssh squidward@192.168.1.106 -p 2600
Password: 0ctopus

We move 1 directory back and we find a file with .sql extension.
By observing its content, it seems to be base64 encoded.

After decoding and observing the contents we see user names and their associated passwords in hashes.

We browse Crackstation to find the values.

Privilege Escalation
Accessing SSH and grabbing the user flag.
$ ssh dirtysalmon@192.168.1.106 -p 2600
Password: crabby4eva

We check for kernel version.

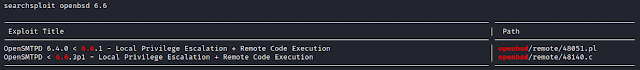
Searching for kernel exploit.
We transfer the exploit on the target machine and give full permission to the file.
We run the exploit and grab the root flag.






Comments
Post a Comment