Prime:1 - Walkthrough [Vulnhub]
Here's my solution for Prime:1.
The machine can be downloaded from here.
Nmap
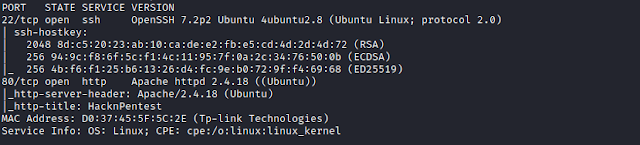
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.105
We find 2 ports open.
Directory Scanning
Browsing the web and checking the source, we did not find any hints.
Using dirb to scan for directories.
$ dirb http://192.168.1.105 -r

Browsing /wordpress, we find that it is build on CMS- Wordpress. We can also see a post, made by the author- victor.
Using wp-scan to enumerate all plugins and users.
$ wp-scan --url http://192.168.1.105/wordpress -e ap,u
We did not find any plugins, but found a user- victor, which we already know.
At this point, tried brute forcing the login as well as the ssh, but no result.
Seems that we need to enumerate more.
Lets use dirb again, but this time we include the extensions.
$ dirb http://192.168.1.105 -X .php,.txt,.html

Browsing /secret.txt, gives us the hint that there is a hidden parameter on php page, and if we get the right parameter,
we have to follow the next step, that is to browse the location.txt for the next move.

We find the hidden parameter- file, on /index.php
Browsing, http://192.168.1.105/index.php?file=location.txt

This gives the hint- we need to use- secrettier360, as a parameter on some other php page.
We can use it on /image.php, which is vulnerable to LFI.

Again we get the hint- for the password file.
Getting Access
Now we have the credentials as-
User: victor
Password: follow_the_ippsec
We browse- http://192.168.1.105/wordpress/wp-login.php , and we login with the found credential.
Navigate to Appearance>Theme Editor.
We select the theme file as- secret.php, to place the php reverse shell payload.
As this is only the file in which we can write.

To run the exploit we browse- http://192.168.1.105/wordpress/wp-content/themes/twentynineteen/secret.php
And on the other hand we start the netcat listener.
We get the reverse shell.
User Flag.
Privilege Escalation
From www-data > saket.
Checking for sudo rights.

While executing the file, we see that it asks for password.
We find a file named as- backup_pass, under /opt/backup/server_database directory, which contains
the password for the file- enc.

Executing the file again. We enter the password as- backup_password

We see 2 new files- enc.txt and key.txt

The file key.txt, says to convert the string- ippsec to md5.

The contents of file- enc.txt, seems to be base64 strings encrypted with AES.
Browsing Devglan to decrypt.
We get the output in base64, decoding it.

We get the password as- tribute_to_ippsec.
Switching to saket.
su saket
Password: tribute_to_ippsec

From Saket > Root.
Lets check for sudo rights.

While executing the file, we see that it looks for a file- challenge, under /tmp directory.

Now under /tmp directory, we create a file named as- challenge, with the payload.

We run the file again.
Root Flag.


















Comments
Post a Comment