Sunset:Twilight - Walkthrough [Vulnhub]
Here's my solution for Sunset:Twilight
The Machine can be downloaded from here.
Nmap
Scanning for all TCP Ports.
nmap -sC -sV -p- 192.168.1.107
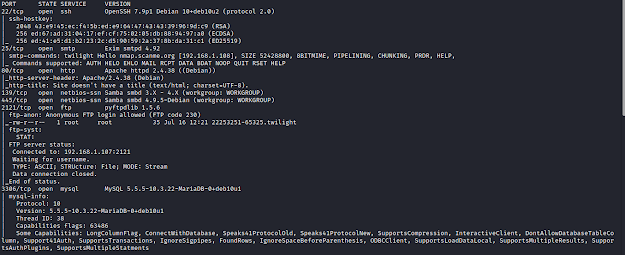

We find 9 open ports.
Enumeration
Browsing the web, navigating to Change language URL, we find that it is vulnerable to Directory Transversal.


Scanning directories using gobuster,
gobuster dir -u http://192.168.1.107 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt

We find an interesting directory /gallery, which allows to upload jpeg images.

While emumerating SMB shares, we find that we have access to share named as- WRKSHARE

Lets get the smbshell.

Now, we place a php reverse shell file named as shell.php, in var\www\html directory.

To execute the shell.php, we browse http://192.168.1.107/shell.php
(We can also browse through the url which is vulnerable to Directory Transversal-
http://192.168.1.107/lang.php?lang=../../../var/www/html/shell.php)
And on the other hand we start the netcat listener.

And we get reverse shell.
Privilege Escalation
Checking the permission on /etc/passwd file, shows we have full permission.
Checking the permission on /etc/passwd file, shows we have full permission.

We change the password for the user- root.
From our machine, we generate a new password for user- root.
From our machine, we generate a new password for user- root.

On the target machine, In /etc/passwd file, we edit the password field for the user- root, and save the file.

Now the user- root, has the password which we have set.

Swtich to user- root.
su root
password: pass
su root
password: pass

User Flag.

Root Flag.




Comments
Post a Comment