Sunset:Decoy - Walkthrough [Vulnhub]

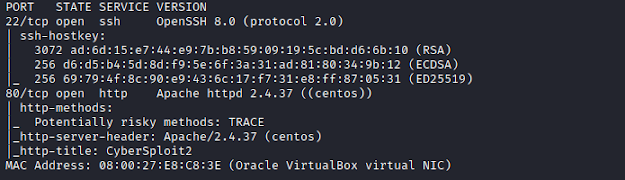
Here's my solution for Sunset:Decoy. The Machine can be downloaded from here. Nmap Lets start by scanning all TCP ports. nmap -sC -sV -p- 192.168.1.106 We find 2 TCP ports open. Enumeration Browsing the web, shows up with a zip file. Download save.zip file. We see that the zip file is protected with password. Lets crack it, extracting the hashes from zip file. Brute forcing against the hashes. We get the password as- manuel As we have the password, unzip it. The shadow file, contains the encrypted password for user- 296640a3b825115a47b68fc44501c828 Lets crack it. Now we have user and password. User: 296640a3b825115a47b68fc44501c828 Password: server Getting Access ssh 296640a3b825115a47b68fc44501c828@192.168.1.106 password: server We get the access, but we see that we are in restricted bash, lets escape this. Connecting again, ssh 296640a3b825115a47b68fc44501c828@192.168.1.106 -t "bash --noprofile" password: server Adding /usr/bin to PATH Privilege Escalation Transfer the...