Hemisphere:Gemini - Walkthrough [Vulnhub]
Here's my solution for Hemisphere:Gemini.
The machine can be downloaded from here.
Service Discovery
Using Nmap for scanning all TCP ports.
$ nmap -sC -sV -p- 192.168.1.132
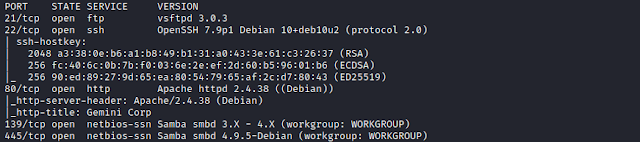
We find 5 ports open.
Enumeration
Browsing the web.

Using gobuster to scan directories.
$ gobuster dir -w /usr/share/wordlists/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.1.132/ -t 100 -x php,txt,html

Browsing /Portal

We click on CONTACTO, we find that the view= parameter is vulnerable to LFI.

By looking at the contents we find a user- william.
By exploting the LFI we try to get the william's ssh key.

We copy the ssh key to a file.
Initial Access
Before accessing ssh. We change the permission of the key file.
$ chmod 600 key
$ ssh -i key william@192.168.1.132

User Flag.

Privilege Escalation
Checking the permissions on /etc/passwd file, shows that we have full privileges.

Lets change the root user password.
On our machine we create the password as- pass

On target machine we change the password for user- root by editing the /etc/passwd file.
Lets view the changes.

Lets switch to root and grab the root flag.







Comments
Post a Comment