Relevant:1 - Walkthrough [Vulnhub]
Here's my solution for Relevant:1.
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.109
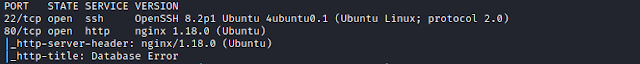
We find 2 port open.
Enumeration
Browsing website, the web page presents us with 3 links, seems some kind of hints, lets check it out.

Browsing the 1st link- https://rb.gy/g5prrv, gets redirect to youtube.

Browsing the 2nd link- https://pastebin.com/sGzQSQXu, seems like a list of credentials.
Just a thought, the home page says- because we hax0r3d your webz!, meaning the hacker has compromised the website.
So, may be they have leaked the credentials here.

Tried brute forcing the ssh but no result.
Browsing the 3rd link- https://ibb.co/JtTY0Md, the QR code.

We can browse Zxing, and decode it.

Interesting, we keep it we may require at further stages.
Lets scan for directories.
$ dirb -u http://192.168.1.109 -r

Seems like the website is built on CMS- Wordpress. We can use wpscan to enumerate it further.
$ wpscan --url http://192.168.1.109 -e ap,u

The wpscan did not recognize the wordpress so we rescan using- force flag.
$ wpscan --url http://192.168.1.109 --force -e ap,u

Still not useful result, now we change the detection mode to- aggressive.
$ wpscan --url http://192.168.1.109 --force --plugins-detection aggressive

We search the exploit for plugin- wp-file-manager and found it here.
Getting Access
After downloading the exploit we run it.

The exploits requires a file- payload.php where we place the php reverse shell payload.

Now to execute the payload we browse- http://192.168.1.109/wp-content/plugins/wp-file-manager/lib/files/payload.php
And on the other hand we start the netcat listener.


We get the reverse shell.
Privilege Escalation
From www-data>news
We find an interesting directory with name- ... (Triple Dots, very confusing name), under /home/h4x0r, let us navigate to it.

A note, let us see what's in it.

Looks like a credential. We verify by checking the /etc/passwd file, the user- news is present.
The password seems to be in hash.

We can browse Crackstation for cracking the hash.

Lets switch to user- news.
$ su news
Password: backdoorlover

From news>root
We check for SUDO rights.
Lets escalate and get the root flag.






Comments
Post a Comment