Misdirection:1 - Walkthrough [Vulnhub]
Here's my solution for Misdirection:1.
The machine can be downloaded from here.
Nmap
Scanning for all TCP ports.
$ nmap -sC -sV -p- 192.168.1.109
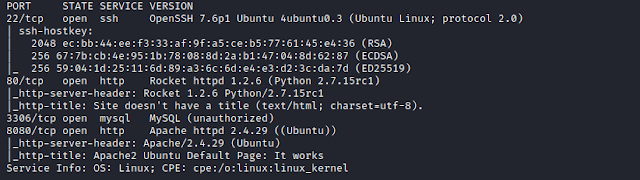
We find 4 ports open.
Directory Scan
Browsing the web and checking the source did not reveal any hints.

From nmap's output we see that http service is also running on port 8080, lets browse it.

Still did not find any hints.
Using dirb to perform directory scanning.
$ dirb http://192.168.1.109:8080/ -r

Browsing /debug directory, we find a web-cli and we see that commands are running fine.

Getting Access
We encode the bash reverse shell payload in base64 format.

Before running it, on the other hand we start the net cat listener.

We get the reverse shell.
Privilege Escalation
From www-data > brexit
We check for sudo rights.

We see that, we can run /bin/bash as user- brexit.

User Flag.

We have full permission on file- /etc/passwd.

We can change the password for user- root.
On our machine we create a password as- password.

On target machine, In /etc/passwd file, we edit the password field, for the the user- root and save the file.
Now the user- root, has the password which we have set.
Switching to Root.
$ su root
Password: password

Root Flag.







Comments
Post a Comment