MoneyHeist:1 - Walkthrough [Vulnhub]
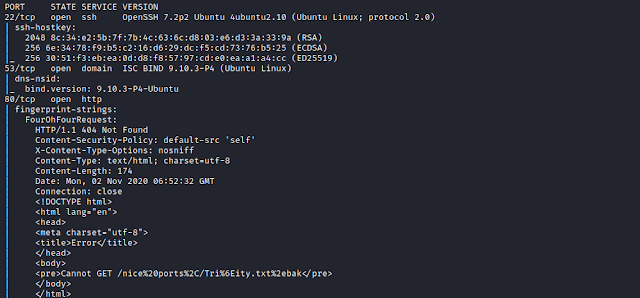
Here's my solution for MoneyHeist:1. The machine can be downloaded from here. Port Scanning Using nmap to scan all TCP ports. nmap -sC -sV -p- 192.168.1.104 We find 5 ports open. Enumeration Browsing the web. We see we have an option to register. After registering we login. The page says- No flag and only the admins will get it. We can guess this can be related with user id, user role, cookies etc. We start the Inspect Element and navigate to Storage Tab > Cookies. Interesting, here we find the presence of JWT tokens in cookies. Lets decode it. We browse the website JWT and decode the value. We find the token uses HS256 algorithm. Now we put the key into a file and run hashcat against it. $ hashcat -m 16500 key.hash /usr/share/wordlists/rockyou.txt We get the secret key as- professor. We again browse the JWT website and try to create a forge token. We place the secret key in the Verify Signature section and alter the email's value to- admin. Now we copy this forged token...


